Penetration Testing Without false-positives
Provide a real shield for your software
Don't waste time on trying to understand hundreds of unclear CVEs.
Let us mitigate actual threats relevant to your systems.
Don't waste time on trying to understand hundreds of unclear CVEs.
Let us mitigate actual threats relevant to your systems.
Mapping and Reducing
Attack Surfaces:
We give a clear mapping of relevant attack
vectors and surfaces, minimize the attack
surface access and reduce the
number of critical endpoints.
Automated Fixing
of 1-days:
We inform about relevant known vulnerable
libraries and code for attack surfaces.
We also give recommendations for possible
minimal updates to eliminate those threats.

Manual Repeated Penetration
Testing:
Our expert researchers will find vulnerabilities in your systems and then our white-hat attackers will show a possible attack scenario, followed by a complete fix of it.
This process is repeated untill no more risks are found.

Generic Mitigations:
We offer powerfull mitigation solutions that will ensure
immediate frustration for all possible attackers.

We believe that the best security defence can be done by the greatest attackers.
All our experts have an experienced background of security R&D in agencies worldwide.

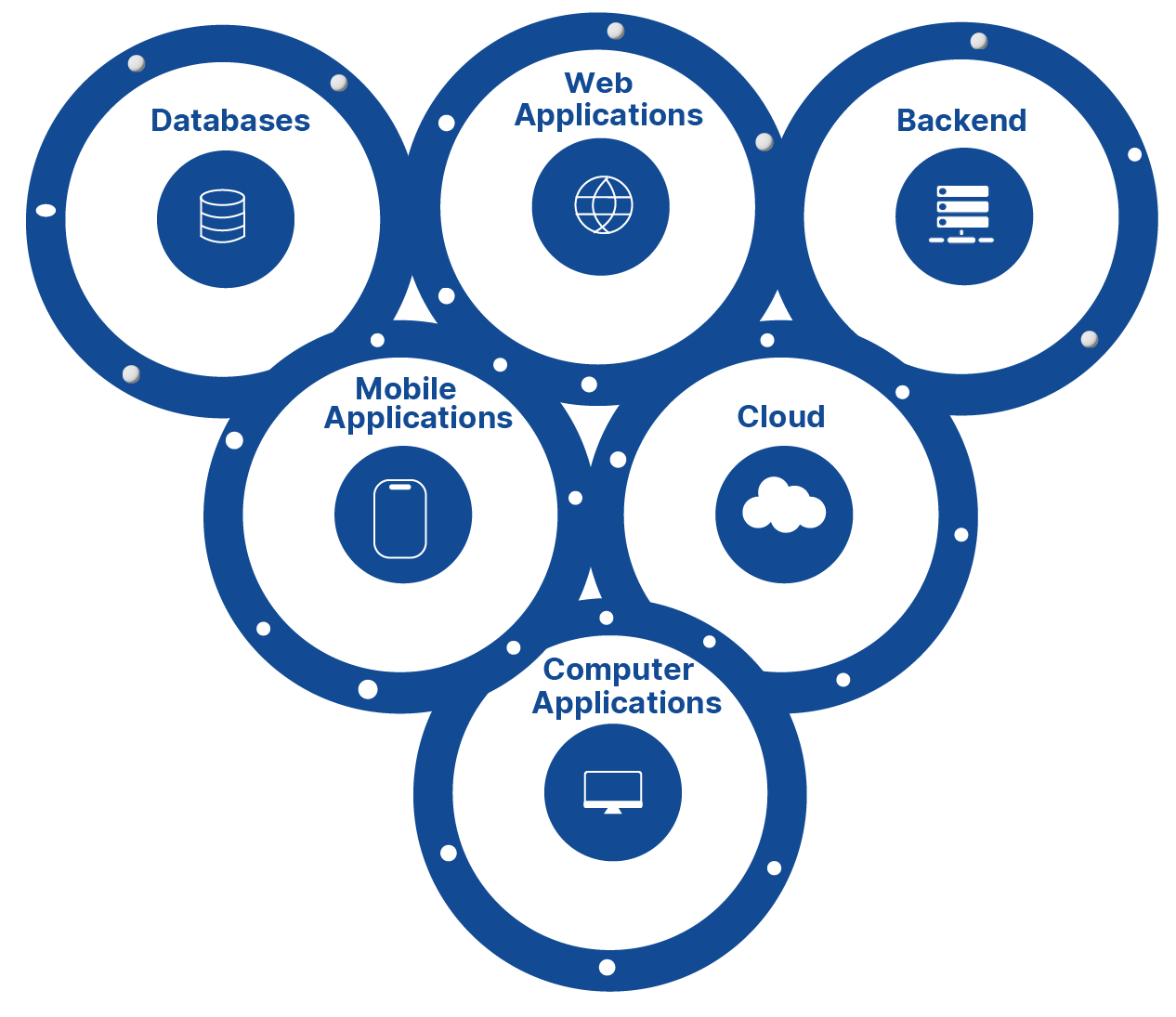
Apex shielding is for all parts of your system:
Contact Us
Mapping and Reducing
Attack Surfaces:
We give a clear mapping of relevant attack
vectors and surfaces, minimize the attack
surface access and reduce the
number of critical endpoints.
Automated Fixing
of 1-days:
We inform about relevant known vulnerable
libraries and code for attack surfaces.
We also give recommendations for possible
minimal updates to eliminate those threats.

Manual Repeated Penetration
Testing:
Our expert researchers will find vulnerabilities in your systems and then our white-hat attackers will show a possible attack scenario, followed by a complete fix of it.
This process is repeated untill no more risks are found.

Generic Mitigations:
We offer powerfull mitigation solutions that will ensure
immediate frustration for all possible attackers.

We believe that the best security defence can be done by the greatest attackers.
All our experts have an experienced background of security R&D in agencies worldwide.

Apex shielding is for all parts of your system:

Contact Us
We give a clear mapping of relevant attack vectors and surfaces, minimize the attack surface access and reduce the number of critical endpoints.
Mapping and Reducing
Attack Surfaces:


Automated Fixing
of 1-days:
We inform about relevant known vulnerable libraries and code for attack surfaces. We also give recommendations for possibleminimal updates to eliminate those threats.

Manual Repeated Penetration
Testing:
Our expert researchers will find vulnerabilities in your systems and then our white-hat attackers will show a possible attack scenario, followed by a complete fix of it.This process is repeated untill no more risks are found.
We offer powerfull mitigation solutions that will ensure immediate frustration for all possible attackers.
Generic Mitigations:
We believe that the best security defence can be done by the greatest attackers.
All our experts have an experienced background of security R&D in agencies worldwide.

Apex shielding is for all parts of your system:

